- 26 Nov 2020
- 6 Minutes to read
-
DarkLight
IoT: How Smart Stuff is Reshaping Ediscovery
- Updated on 26 Nov 2020
- 6 Minutes to read
-
DarkLight

For many, gone are the days when the only place you looked for evidence was a file cabinet or Bankers Box. The internet revolutionized how humans interact and communicate and as a result reshaped how and where practitioners look for key legal evidence. The first major impact on evidence came in the form of email and relatively shortly thereafter social media. The mid-2000s ushered in the iPhone and with it, a veritable app-ocalypse of new phone-based games, tools, and methods of communicating and generating electronically stored information (ESI).
The new kid on the ESI block today is the Internet of Things (IoT). The IoT is an ecosystem of over 30 billion web-enabled things (from smartwatches to doorbell cameras to smart refrigerators) that are constantly performing tasks, collecting data, and most in some cases, sharing it. Each of these devices possess a wealth of information about human behavior, movement and many could contain information dispositive to a case or investigation. Several cases have been decided based upon information harvested from IoT devices and that number is likely to grow significantly in the coming years.
This blog breaks down the types of IoT devices on the market today, potential uses for ESI from IoT devices, and considerations and challenges in dealing with IoT data in your ediscovery workflow.
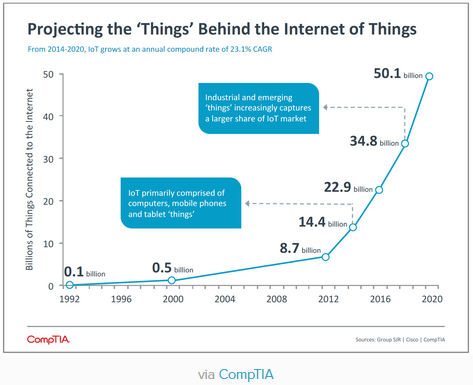
via CompTIA
What is the IoT?
IoT refers to the network of physical objects (things) that are embedded with sensors, software, and other technologies to connect and exchange data with other devices or systems via the internet. The first device in the IoT ecosystem was a soda vending machine at Carnegie Mellon University that was connected to ARPANET (the precursor to the internet as we know it) in the ‘70s.
The term itself was not coined for another nearly 30 years, and really did not begin to see exponential growth until the introduction of Wi-Fi and 4G in the 2010s. Today, 127 devices are added to the IoT ecosystem each second and the current volume of devices is anticipated to double by 2025. 5G and a shift from IPv4 to IPv6 (which increased the number of IP addresses available and thus, the number of devices that could connect to the internet) are both likely to fuel this growth velocity.
IoT devices run the gamut but are loosely categorized into five main categories:
- Consumer IoT: Stuff you might use directly like smart cars, fitness wearables, and home automation
- Commercial IoT: Organizational-level devices in smart healthcare, transportation, logistics, and building automation
- Industrial IoT: Smart devices relating to agriculture and manufacturing
- Infrastructure IoT: Smart cities with operations of sustainable urban and rural infrastructures, monitoring energy and environmental impact
- Military IoT: Smart devices for reconnaissance, surveillance, and other combat-related objectives
IoT devices as ESI sources
From smart cars or TVs to Fitbits and Amazon Alexa, there is a proliferation of IoT in our daily lives. As these IoT devices have become commonplace, they have created a vast digital fingerprint that savvy legal practitioners are beginning to mine for ESI.
Fitness wearables
Fitbits and other networked wearable fitness devices are all the rage, and their comprehensive biometric tracking has been used as evidence to disprove personal injury claims when the claimant was exercising despite claiming grievous injuries. Like Edgar Allan Poe's “The Tell-Tale Heart,” the spikes in heart rate from wearable data have been pivotal in these cases.
Logistics trackers
Large logistics and shipping organizations have begun employing web-enabled trackers across their fleet of vehicles over the last few years. Data from these trackers (electronic control modules) has found its way into personal injury and property damage cases and the lack of defensible preservation of this data has resulted in claims of spoliation.
Smart home devices
Amazon Echo and Dot and Google Home have been high on holiday gift lists for the last several years. As these omnipresent ever-listening devices have sprung up in homes and hotels, they are increasingly turned to as a source of evidence of crime. In the most well-known case, a combination of Amazon Alexa and a smart water meter were hotly contested sources of evidence in a murder case that hinged on the 3 a.m. draining and refilling of a hot tub!
Smart medical devices
The impact of biometric and medical tracking does not stop with wearables. Web-enabled internal and external medical devices possess a wealth of evidence. One arson case was decided based upon the data obtained from a web-enabled pacemaker that undermined a defendant’s claims in an arson case.
Smart cars (and more)
Most cars today, not just Tesla, collect, record, and transmit potentially relevant ESI. GPS sends and receives information about location and speed, and the development of autonomous vehicles creates another can of worms entirely.
Considerations with IoT evidence
As with every new entrant to the ESI dataverse, the IoT sources bring their own set of challenges. From data formats to increased risk of spoliation and privacy concerns, there is a minefield — and practitioners should tread lightly.
Remembering to include it!
For many legal practitioners, IoT data is not the first thing that is considered when scoping for ediscovery and data requests. The first step is to expand your custodial interview and ESI scoping questions to include potentially relevant sources of ESI. Most corporate legal departments have yet to include IoT data in their data governance or litigation response plan so it is important to raise the issue and reevaluate your data governance to include it. Additionally, specificity is key in making requests for IoT data, especially because it is a data type that may be unfamiliar to many respondents.
Data privacy
IoT devices have raised privacy concerns in terms of the data that is collected and shared by the devices and various litigation and regulations exist to face that challenge. As privacy considerations relate to ediscovery, the Stored Communications Act (SCA) generally prevents providers of electronic communication services from divulging private communications. That being said, the SCA does not preclude the court from requesting the data from the person in physical possession of a smart device (Flagg v. City of Detroit).
Spoliation
As with email, a lack of understanding about IoT will not excuse intentional or inadvertent spoliation. However, the wide variety of IoT devices have an increased susceptibility to data modification and destruction. Something as simple as restarting the device, interrupting its power supply, disabling its internet connection, or perhaps even just moving it out of range of its known internet access point so that it cannot sync its data to the cloud can all impact the data integrity of some smart devices. Additionally many IoT devices have very short windows of time before data is overwritten or automatically erased, so determining a preservation approach quickly should be a top priority.
Gaining access
Large enterprises with IoT products are not always forthcoming with providing the ESI from their smart devices. In a murder case involving Alexa data, Amazon fought for years before ultimately turning the data over. It is also important to consider the device owner’s actual “possession, custody, or control” under Rule 34 — this question is complicated due to the web-enabled nature of the devices.
Data headaches
Data generated by IoT devices does not always play nice with traditional ediscovery platforms. It is important to understand the data format you are engaging with, any potential limitations, and what level of usability the technology you rely on will provide the data for you.
Don’t be an IdioT with IoT
The velocity of IoT proliferation shows no signs of abating. It will serve practitioners well to begin to include this data source in their data governance policies, data mapping, and most importantly, their ESI scoping at the outset of a case. Key information often resides in this evolving data category and, as with any other data source, the specter of spoliation looms large if it is excluded or mishandled.
By: Cat Casey
DISCO - ediscovery Solutions
As the leading provider of software as a service solutions developed by lawyers for lawyers, DISCO is reinventing legal technology to automate and simplify complex and error-prone tasks that distract from practicing law

